The top 10 blog posts on BitVPN let us know a VPN is used for multiple reasons. Either for fun or cybersecurity tips, a VPN is a must-have tool as you use the Internet. If you still don’t know about the functions of a VPN, here’s a chance to get them back.
#10. Cybersecurity Tips for Remote Workers
The leading change brought by COVID-19 lies in the work mode changing from offline into online. With more personal devices and network taking part in online communications and interactions, more online risks are also seen with so many cyberattacks occurring. A VPN connects personal devices with corporate network to stop corporate data from breaches. Nevertheless, some cybersecurity tips should be also conformed to so as to avoid prying eyes, hackers or cybercriminals.

#9. Secure Your WiFi in Simple Steps
Neither public WiFi nor personal WiFi is secure unless a VPN is used. Public WiFi allows all to access even without a password. Once you get your device connected with it, you’ll directly become the target of hackers. When it comes to your personal WiFi for which a password is usually set by yourself, however, it directly leads your device with the Internet so that your Internet Service Provider, or ISP, will know all your online activities based on your IP address. With a VPN used, you’ll be able to keep anonymous online, stopping any suspicious parties from tracking you on the Internet.

#8. Unblock School WiFi with a VPN
There’s no doubt that a VPN is a must-have tool for school or campus students because the network at campus or school is limited so that students fail to visit all the content on the Internet like streaming, social media, torrenting, etc. A VPN can break school WiFi restrictions and bypass school network control.

#7. Beat Netflix VPN Ban with BitVPN
It’s an ordinary idea to use a VPN to beat Netflix geological restrictions. However, Netflix conforms to strict catalogue policies so that some VPNs fail to beat the Netflix VPN ban. BitVPN can beat the Netflix VPN ban in a decentralized way so that its users are able to enjoy their streaming service around the world.
#6. Everything a VPN Beginner Needs to Know
It’s glad to see people striving to protect their cybersecurity and online privacy every year. This blog post sees its popularity in almost every year, which shows that an increasing number of people care about their online security and privacy when using the Internet.

#5. How to Speed Up Your Internet
Nothing is more annoying than a slow network. Nowadays, people hold extremely little patience towards even a little buffering. Moreover, there’s a myth that a VPN will make your Internet slow down. If you do believe so, this blog post is perfect for you with lots of useful tips to speed up your network contained.

#4. Avoid Getting Banned on Chinese Apps in India
It’s one of the happiest moments this year that is to hear about some Indians speaking of the capability of BitVPN helping them to regain freedom to Chinese applications. So much of our life depends on a small application in your mobile and once it fails to be used, your life will be severely affected, and your customers will possibly fail to be contacted. The reason why this blog post is so popular lies in its usability.
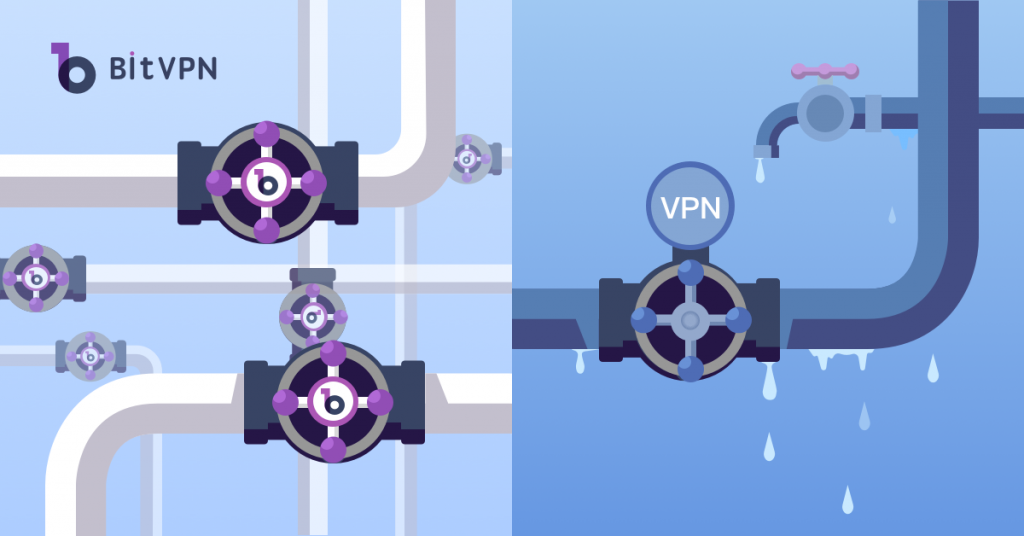
#3. Centralized VPN vs Decentralized VPN
Want to know the difference between centralized VPN and decentralized VPN? This blog post is worth reading. Recent years have witnessed data breaches of VPNs, which is especially true on free VPNs. Well, the essential disadvantage of centralized VPNs (most VPNs on the market) accumulates users’ data in a single server. Once it gets hacked, all users’ data will be leaked. A decentralized VPN, however, scatters users’ data to multiple servers or nodes so that users’ data will be well protected against any leak or hack.
#2. Encrypt Your Internet Traffic in a Decentralized Way
Everyone should encrypt their internet traffic but not everyone knows that. As you use the Internet, your online tracking isn’t what can be seen only by you. Internet fraudsters and third-party organizations are keeping tabs on your internet activity. Your Internet activities are always monitored by those people who have been striving to get more profits. Therefore, it would be weird and dangerous not to get some protection when you use the Internet for anything. There are multiple ways out there that can be used to protect your Internet connection from snooping eyes. Well, a decentralized way is an optimal solution.
#1. Can My Phone be Hacked through Bluetooth?
Bluetooth technology is built into all cell phones and other devices. Bluetooth connection allows quick and easy connection of phones with headphones, speakers, TVs, and other devices with Bluetooth technology built-in. However, do you know that sometimes it’s Bluetooth that may expose your phone to being hacked by someone? This blog post will tell you.

- How to Tell if Someone is Spying on My Phone and How to Stop That
- Ask Your Employees These Questions to Easily Test Their Cybersecurity Awareness
- What’s Computer Hacking and How to Prevent It
- What is Ransomware? Everything You Should Know About Top 1 Possible Cyberattack in 2021
- Affected by Facebook Leak? How to Stay More Private on Social Media
