Online dating has seen its rocketing popularity in recent years. Based on a report on online dating released by Kaspersky daily, one in three users are doing online dating. Moreover, quite a large number of people have found love from online dating. However, apart from online romance, online risks are also available, possibly leading to virus infection or data breaches and you can fight against them with a few simple tips.
IT Security Risk Types You May Suffer from Online Dating Websites and Apps
Those who usually date online often suffer from more IT security incidents than those who don’t, which can be seen from the image below published by Kaspersky daily.
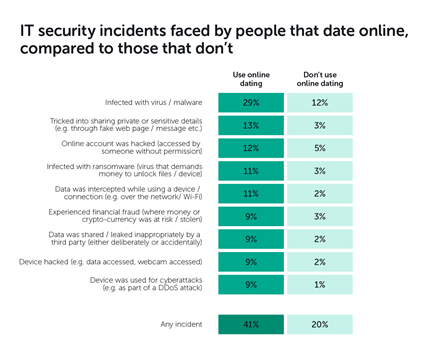
The leading IT risks online daters will meet include the following types.
The device is easy to be infected by viruses such as spyware, malware, etc. while dating online.
Malware is a type of malicious software that can be rooted in your computer to access or damage your computer without your knowledge. If your computer is infected by spyware, your personal information will be stolen and passed to advertisers, data groups,s or any organization calling for your personal information for profit.
The personal information spyware targets include your bank account information and any personal information referring to your identity. Worse still, spyware can monitor your online activities, login username and password, and your sensitive information.
Then how exactly does your device get infected by spyware during online dating?
On one hand, your computer may get infected by spyware just through the online dating website or app. Some online dating websites or apps are created to accumulate their users’ personal information through spyware and they are fake websites or apps but perform like real ones such as Tinder, Grindr, Plenty of Fish, etc.
On the other hand, as you massage your dates through an online dating service platform, some scammers possibly send you short URL links to seduce you to click them. As you click them, those malicious links will automatically root spyware inside your computer so that all your online activities will be able to be tracked at any time.
Spyware, however, aims to get money by accessing users’ online data and blackmailing victims.

You may suffer from data breaches or leaks when using online dating websites or apps.
It’s quite easy for you to lose your online data through online dating activities, which is especially true as you expose too much of your personal information to dates in your profile or in the process of messaging with dates.
The personal information sharing that may lead to data breaches or data leak includes:
- Full name
- Birthday
- Home address
- Place of work
- Personal email address
- Personal phone number
- Any credit card or bank account details
- Information about your children
- Your salary
If such information gets leaked during online dating, your real identity will be able to be accurately tracked with the help of social media account information.
You may suffer from catphishing when using online dating websites or apps.
Some scammers usually date people on online dating websites or apps through fraudulent identities and their final aim is to gain money. They behave like cats that use a capper to attract fish. Based on fraudulent identities, they try to get victims’ personal information like passwords or credit card details.
Multiple advantages that may be brought by catphishing drive catphishiers to create frauds on online dating websites or apps. They establish “reliable” images to let dates trust them and any chance may be searched to transfer money to them.
Online dating frauds also aim to get personal information from their dates by stealing their photos or other information that finally indicates the identity of victims.
How to Tell You’re Actually or Possibly Suffering from Above IT Risks during Online Dating
It’s not horrible to suffer from IT risks but it’s even more horrible that you haven’t known that.
You should learn about the signs indicating that you’re actually suffering from IT risks during online dating or about to.
How to tell your device has been infected by malware or spyware
Knowing the signals below is useful to identify malware and get rid of the malware.
Malware Signals on PC
- Your device runs slowly.
- More ads than normal appear on your screen.
- Your system breaks down without any reason.
- The disk space is mysteriously lost.
- Your system’s internet activity goes up.
- The homepage of your browser is changed without your permission.
- Some new toolbars, extensions, or add-ons suddenly appear on your browser.
- Your antivirus software suddenly stops working.
Malware Signals on Android Devices
- Invasive ads suddenly appear on your screen.
- Data usage increases without your expectation.
- There are bogus charges on your bill.
- Strange phone numbers or SMS appear on your contact list.
- When your Android phone’s performance lags, your phone gets heated.
- Devices are automatically connected to WiFi or the internet.
Spyware Signals on PC
- Your device runs slow.
- Apps take more time to load than before.
- The battery drains faster than normal.
- Pop-up ads become suddenly more.
- There are “unknown” apps on your device and you don’t remember downloading.
- Unexplained data usage occurs.
- Higher phone bills arrive.
How to tell you’re suffering from data breaches or data leak
The following signals tell you’re suffering from data breaches or data leaks:
- Your computer or smartphone runs at a low speed.
- A number of pop-ups or intrusive ads go up abruptly.
- You have accounts that can’t be logged in with the password you kept in mind.
How to tell your date is possibly catphishing you
The following signals should be remembered to analyze whether your date is catphishing you:
- They ask for your personal information.
- They cancel the meeting plan at the last minute.
- They seem too excellent to be true.
- They suddenly talk about economic trouble during your talk.
- They refuse video chat.
- Few social activities sharing is seen on their social media accounts.
.png)
How to Protect Yourself Against IT Risks Caused by Online Dating – Handy Tips
Account Security Tips
- Use strong passwords or two-factor authentication for your Internet accounts.
- Don’t include personal information in your profile.
- Use a secure WiFi network when using online dating websites or apps. If you can’t guarantee that, use a VPN.
- Never allow an online dating account to have access to your geological location.
Social Engineering Security Tips
- Don’t click any link you receive, especially those using shortened URLs.
- Don’t open any file you receive on online dating websites or apps.
- If you find a suspicious online dating account, you can use its image to Google him or her. If the image derives from a model company or a foreign celebrity, the account is perhaps a fake one.
- Avoid leaking information related to your personal information.
- Never transfer money to anyone you know on online dating websites or apps.
Privacy Security Tips
- Avoid linking online dating accounts with social media accounts like Facebook since it’s easy to leak your online data.
- Avoid linking online dating accounts with personal phone numbers. Use a temporary number instead. That also applies to personal email addresses.
- Never share your private photo with your dates while dating online.
- Use a VPN on your device to protect against prying eyes on the Internet.
Bottom Line
It’s quite easy to suffer from IT security risks when you date online.
There are some signals telling you your device gets infected by a virus or you suffer from data breaches or data leaks.
Some useful and easy tips should be learned to protect against IT security risks caused by online dating.
FOLLOW US
- How to Tell if Someone is Spying on My Phone and How to Stop That
- Ask Your Employees These Questions to Easily Test Their Cybersecurity Awareness
- What’s Computer Hacking and How to Prevent It
- What is Ransomware? Everything You Should Know About Top 1 Possible Cyberattack in 2021
- Affected by Facebook Leak? How to Stay More Private on Social Media